Last Modified: 26.10.2021
|
|
|
Views: 4631
Last Modified: 26.10.2021
Passwords are sent openly, when the
SSL
SSL (Secure Sockets Layer — protected sockets level) — cryptographic protocol that ensures secure connection. It employs asymmetric cryptography for key exchange authentication, symmetric encoding for saving confidentiality, message authentication codes for message integrity.
Secure authentication - feature that ensures user password encryption. Password encryption is not a replacement for SSL. Secure authentication protects from password search attack only during traffic interception.
When an intruder has an opportunity to change traffic, the encryption won't help. Changing traffic is more of a complex task than intercepting it (i. e. freely broadcasting WiFi). Moreover, password encryption doesn't protect from session interception; the session has its own protection mechanisms (IP-binding, session code frequent update). In general, level of protection has increased, but such features as SSL are more preferable.
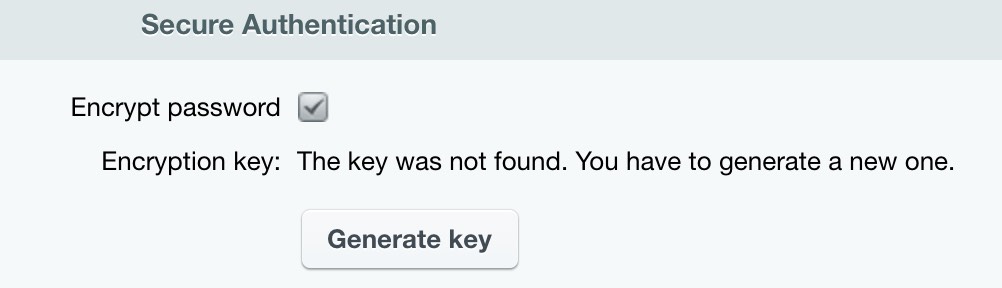
Connect Secure authentication in the main module settings inside the Authentication tab:
Note: click Apply to save module settings after selecting the checkbox before generating the key. Without this action, no key will be generated.
Clicking on Generate key creates RSA RSA (alphabetic acronym from Rivest, Shamir and Adleman last name) — cryptographic algorithm with public key. . Key size depends on libraries installed on the server. By default, openssl PHP module is used, creating 1024-bit key. It's recommended to use specifically this key format. If module is not installed, you can use bcmath with generating of 512-bit key. If both things are unavailable, you cannot enable encryption. You can only generate a unique key only once. You need to re-generate the key in case of suspicions of compromised key. Attention! Customer computer browsers must have Javascript enabled.
Courses developed by Bitrix24
|