Last Modified: 11.06.2024
|
|
|
Views: 10843
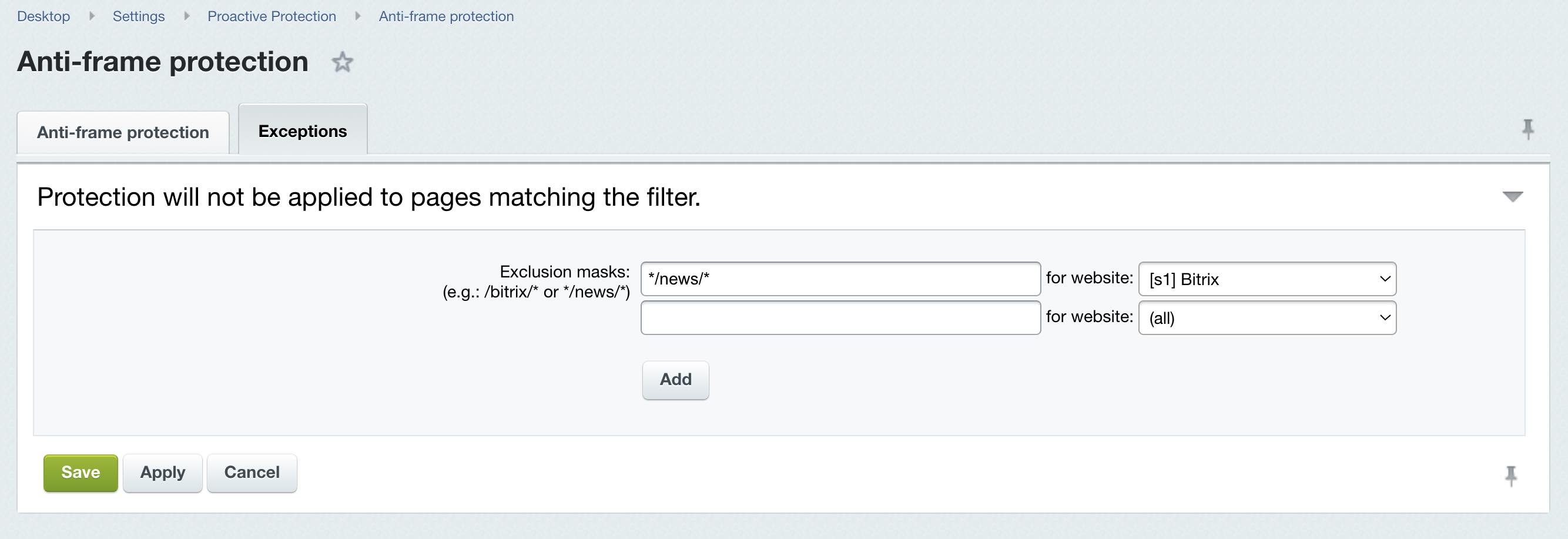
Last Modified: 11.06.2024 The limits on the frame work can be activated/deactivated on the page Anti-frame protection (Settings > Proactive Protection > Anti-frame protection).
The prohibition to use of cross-domain frames referring to resource pages is introduced by setting the header X-Frame-Options to the value SAMEORIGIN. X-Frame-Options
This header indicates to the browser if website pages can be loaded through <frame>/<iframe>. The DENY value will prohibit loading through frames, the SAMEORIGIN value will permit loading through frames, provided that both the frame and the page that loads such frame are located on the same domain (Same Origin Policy). The main function of this protection consists in preventing click-jacking. As an additional advantage, it will permit you to prevent the attack described by Ben Schmidt. If necessary you can add your page to the exceptions by defining the constant B_SECURITY_FRAME as false before connecting the core. Anti-frame protection in Bitrix24 On-premise editions using BitrixVMBoth Bitrix24 On-premise editions and Bitrix Virtual Appliance have anti-frame protection available inside Bitrix24 control panels. You will find header for anti-frame protection in the nginx config file at /etc/nginx/bx/conf/general-add_header.conf. Such entry looks as follows: add_header X-Frame-Options SAMEORIGIN; The same header is added when you enable anti-frame protection using the proactive protection module. And, you can configure exceptions, if such header is not required, for different Internet metrics and analytics services. BitrixVM with standard settings can have a situation, when nginx config overlaps the general system anti-frame protection setup. In this case, header will be always available, even if disabled in the control panel settings. But, with anti-frame protection enabled, header will be duplicated and sites added as exceptions to anti-frame protection - won't work correctly. A solution for such situation is to use only a single tool. It's recommended to use Anti-frame protection feature available in Bitrix24 to avoid necessity of regular updates for server config files. You can comment out the header once in the file /etc/nginx/bx/conf/general-add_header.conf for BitrixVM: #add_header X-Frame-Options SAMEORIGIN; And then you can enable anti-frame protection via Proactive protection > Anti-frame protection. Now X-Frame-Options header will be written correctly and you can add exceptions via control panel, without changes to server configuration files.
Courses developed by Bitrix24
|